Want to understand the latest advancements in cybersecurity? This article features the top 3 cybersecurity influencers of 2024.
By examining their contributions to threat detection and encryption advancements, we’ll gain a deeper understanding of their work in this field.
Understanding Cybersecurity? A Beginner’s Guide
Cybersecurity can seem like a complex and ever-changing landscape. But at its core, it’s about protecting the things that matter in our digital world: information, systems, and devices. Here’s a breakdown to help you understand cybersecurity:
The Big Picture:
- What it is: Cybersecurity is the practice of protecting internet-connected systems, including hardware, software, and data, from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Why it’s important: Our lives are increasingly reliant on technology. Breaches can lead to identity theft, financial loss, and disruption of essential services.
The Three Pillars of Data Security:
- Confidentiality: Ensuring only authorized users can access your information.
- Integrity: Guaranteeing data remains accurate and hasn’t been tampered with.
- Availability: Making sure your information and systems are accessible when needed.
Common Threats:
- Malware: Malicious software like viruses, worms, and ransomware that can harm your devices or steal data.
- Phishing: Deceptive emails or messages designed to trick you into revealing personal information or clicking malicious links.
- Social Engineering: Exploiting human psychology to manipulate you into giving away sensitive information or taking actions that compromise security.
Building Your Defenses:
- Strong Passwords & Multi-Factor Authentication (MFA): Use complex, unique passwords and enable MFA for an extra layer of protection.
- Software Updates: Keep your operating systems, applications, and firmware updated to patch security vulnerabilities.
- Firewalls & Anti-virus Software: These tools act as shields, filtering incoming and outgoing traffic and preventing malware infections.
- Data Backups: Regularly back up your data to ensure you have a copy in case of a cyberattack or system failure.
Staying Informed & Vigilant:
- Be skeptical of unsolicited emails and messages. Don’t click on suspicious links or attachments.
- Think before you share. Be mindful of what information you share online.
- Stay updated on cybersecurity threats. Learn about common scams and how to protect yourself.
Remember, cybersecurity is an ongoing process. By understanding the basics and implementing these steps, you can significantly improve your online safety and protect yourself from cyber threats.
What is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users via ransomware; or interrupting normal business processes.
Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
Cybersecurity is all about protecting our stuff in the digital world. This includes things like computers, phones, tablets, and even the networks that connect them. Cybersecurity professionals try to keep these systems safe from attacks by hackers who might want to steal information, cause damage, or hold our data hostage.
Here’s a breakdown of what cybersecurity protects against:
- Unauthorized access: This means keeping people out of our systems and data who shouldn’t be there.
- Data breaches: Hackers might try to steal personal information like credit card numbers or passwords.
- Malicious software (malware): This is software that can harm our devices or steal data. Viruses, ransomware, and spyware are all types of malware.
- System disruptions: Cyberattacks can take down entire computer networks, causing businesses and organizations to lose money.
Cybersecurity is important for everyone, from individuals to businesses to governments. By taking steps to protect ourselves online, we can help to keep our information safe and secure.
Types of Cybersecurity
The term “cybersecurity” applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
· Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
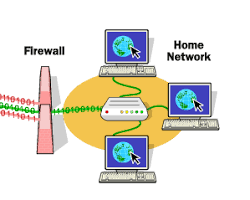
· Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
· Information security protects the integrity and privacy of data, both in storage and in transit.
· Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
· Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
· End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
These are just some of the many types of cybersecurity. By implementing a multi-layered approach that incorporates these different aspects, organizations and individuals can significantly improve their overall cybersecurity posture.

John Strand
John Strand is a cybersecurity expert known for sharing his knowledge generously with others.
As the owner of Black Hills Information Security (BHIS), he leads the development of Hunt Teaming, Command & Control (C2), and Pivot testing.
With over 100 organizations consulting on security, compliance, and penetration testing, John has made significant contributions.
He co-authored “Offensive Countermeasures: The Art of Active Defense” and contributed to the Penetration Testing Execution Standard (PTES).
John also created Black Hat’s “Active Defense, Offensive Countermeasures, and Hacking Back” course and the SANS Institute’s “Hacker Tools, Techniques, Exploits, and Incident Handling” course.
Twitter: 45,048 followers
LinkedIn: 60,800 followers
If you are interested in cybersecurity insights, you can watch all the episodes on their Black Hills Information Security YouTube channel
Kim Zetter
Kim Zetter is an award-winning investigative journalist renowned for her work across various media outlets, including WIRED, The New York Times Magazine, Politico, and The Washington Post.
She is best known as the author of “Countdown To Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon,” about the virus that disrupted Iran’s nuclear plans. The book highlights how a digital attack can possess the same destructive capability as a megaton bomb.
Kim’s contributions to the field have earned her widespread acclaim and established her reputation as a leading authority on digital security issues.
Twitter: 95,201 followers
LinkedIn: 7,000 followers
One of her latest posts on X (formerly Twitter) addresses the vulnerability found in Apple chips.
Kim Zetter is a leading expert in the world of cybersecurity journalism. Here’s a quick rundown on her:
- Investigative journalist and author: She’s been covering cybersecurity and national security for over two decades, breaking important stories on topics like:
- NSA surveillance
- WikiLeaks
- The hacker underground
- Security vulnerabilities in electronic voting machines (one of her award-winning areas)
- Stuxnet expert: She’s a recognized authority on Stuxnet, a powerful computer worm that disrupted Iran’s nuclear program. She even wrote a book about it called “Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon.”
- Highly respected: Her work has been recognized by her peers and security professionals, voting her one of the top 10 security journalists in the US on three separate occasions.
- ** prolific writer:** Her work can be found in publications like Wired (where she spent 13 years), The New York Times Magazine, Politico, Washington Post, Motherboard, and Yahoo News.
Jane Frankland

A prominent figure in cybersecurity, Jane Frankland is not only a successful tech entrepreneur, author, and speaker but also a staunch advocate for women in the industry.
Jane has won awards for her leadership and tirelessly promotes inclusivity. She believes in a future where everyone has opportunities, and she works with companies and organizations, including the UN, to make this vision a reality.
Additionally, she has written two books: “IN Sights” and “IN Security.”
These books address the challenges women face in the cybersecurity field and provide valuable insights to help women navigate and succeed in this male-dominated industry.
Twitter: 12,226 followers
LinkedIn: 33,471 followers
Jane Frankland discussed cybersecurity and women’s empowerment on The Cyber Consulting Room podcast.
Features and Benefits of Cybersecurity
Cybersecurity isn’t a single product, but a set of practices and tools that work together to achieve a secure digital environment. However, we can talk about the features of these practices and the benefits they bring.
Features of Cybersecurity:
- Access Controls: These define who can access what information and systems, ensuring only authorized users have permission.
- Data Encryption: Scrambles data using algorithms, making it unreadable to anyone without the decryption key.
- Data Backup and Recovery: Creates copies of data stored securely, allowing for restoration in case of attacks or system failures.
- Network Security Tools: Firewalls, intrusion detection/prevention systems (IDS/IPS) monitor and filter network traffic, blocking malicious activity.
- Endpoint Security: Protects individual devices like laptops and phones with anti-virus software, firewalls, and encryption.
- Vulnerability Management: Regularly identifies and addresses weaknesses in systems and software to prevent attackers from exploiting them.
- Security Awareness Training: Educates users about cyber threats and best practices for safe online behavior.
Benefits of Cybersecurity:
- Protects Sensitive Data: Safeguards personal information, financial data, intellectual property, and other confidential information from unauthorized access.
- Reduces Risk of Attacks: Cybersecurity measures make it more difficult for attackers to breach systems and steal data.
- Improves Business Continuity: Minimizes downtime and disruptions caused by cyberattacks, ensuring smooth operation of critical systems.
- Enhances Customer Trust: Strong cybersecurity demonstrates a commitment to protecting customer data, fostering trust and loyalty.
- Maintains Compliance with Regulations: Many industries have regulations requiring specific data security measures. Cybersecurity helps organizations meet these requirements.
- Boosts Productivity: Reduced security concerns and fewer incidents lead to a more focused and productive workforce.
- Saves Money: Cyberattacks can be costly. Effective cybersecurity helps prevent financial losses from data breaches and system disruptions.
By implementing these features, organizations and individuals can reap the significant benefits of a robust cybersecurity posture. It’s an investment that safeguards valuable information, fosters trust, and ensures a more secure digital environment.
Guardians of cybersecurity
The cybersecurity battlefield is a dynamic one, with countless brilliant minds constantly innovating.
These 2024 influencers we’ve highlighted stand as prominent figures, their contributions in threat detection and encryption advancements offering crucial footholds in securing our digital future.
It’s vital to recognize their leadership, but their work is far from singular – a vast network of cybersecurity professionals continuously pushes the boundaries of online safety.
This ongoing collective effort is what truly supports a more secure digital tomorrow.
Moreover, if you’re curious about the future of technology beyond cybersecurity, check out our article on the top 3 AI influencers of 2024.
cybersecurity knowledge
Cybersecurity knowledge encompasses a wide range of topics but can be boiled down to protecting information systems and data from unauthorized access, use, disclosure, disruption, modification, or destruction. Here’s a breakdown of cybersecurity essentials:
- Core Concepts:
- Understanding what cybersecurity is and its importance
- The CIA triad: Confidentiality, Integrity, and Availability of data [1]
- Different types of cyber threats and attacks (malware, phishing, etc.)
- Preventive Measures:
- Strong passwords and multi-factor authentication
- Keeping software updated
- Using firewalls and anti-virus software
- Data backups
- Staying Informed:
- Recognizing common social engineering tactics
- Being cautious about suspicious emails and attachments
- Staying informed about current cyber threats
There are many resources available to learn more about cybersecurity. Here are some options to get you started:
- For Beginners:
- More Comprehensive Resources:
What its work Cybersecurity influencers?
Cybersecurity influencers act as educators and thought leaders in the digital security space. Their main role is to raise awareness about cybersecurity threats and best practices to stay safe online. Here’s a breakdown of what they typically do:
- Content Creation:
- They create informative content on various cybersecurity topics through blog posts, social media updates (like Twitter threads), podcasts, or even videos.
- They share their expertise and insights on emerging cybersecurity trends, providing valuable analysis on recent attacks or data breaches.
- Influencers simplify complex concepts for a general audience, offering practical tips and recommendations for individuals and businesses.
- They actively follow the ever-evolving landscape, keeping their audience informed about the latest threats and vulnerabilities.
By leveraging their online presence, influencers can reach a broad audience and make a significant contribution to improving overall posture.
Disclaimer ||
The Information provided on this website article does not constitute investment advice ,financial advice,trading advice,or any other sort of advice and you should not treat any of the website’s content as such.
Always do your own research! DYOR NFA
Coin Data Cap does not recommend that any cryptocurrency should be bought, sold or held by you, Do Conduct your own due diligence and consult your financial adviser before making any investment decisions!




Leave feedback about this