Transmission Control Protocol/Internet Protocol (TCP/IP) is the language a computer uses to access the internet. It consists of a suite of protocols designed to establish a network of networks to provide a host with access to the internet.
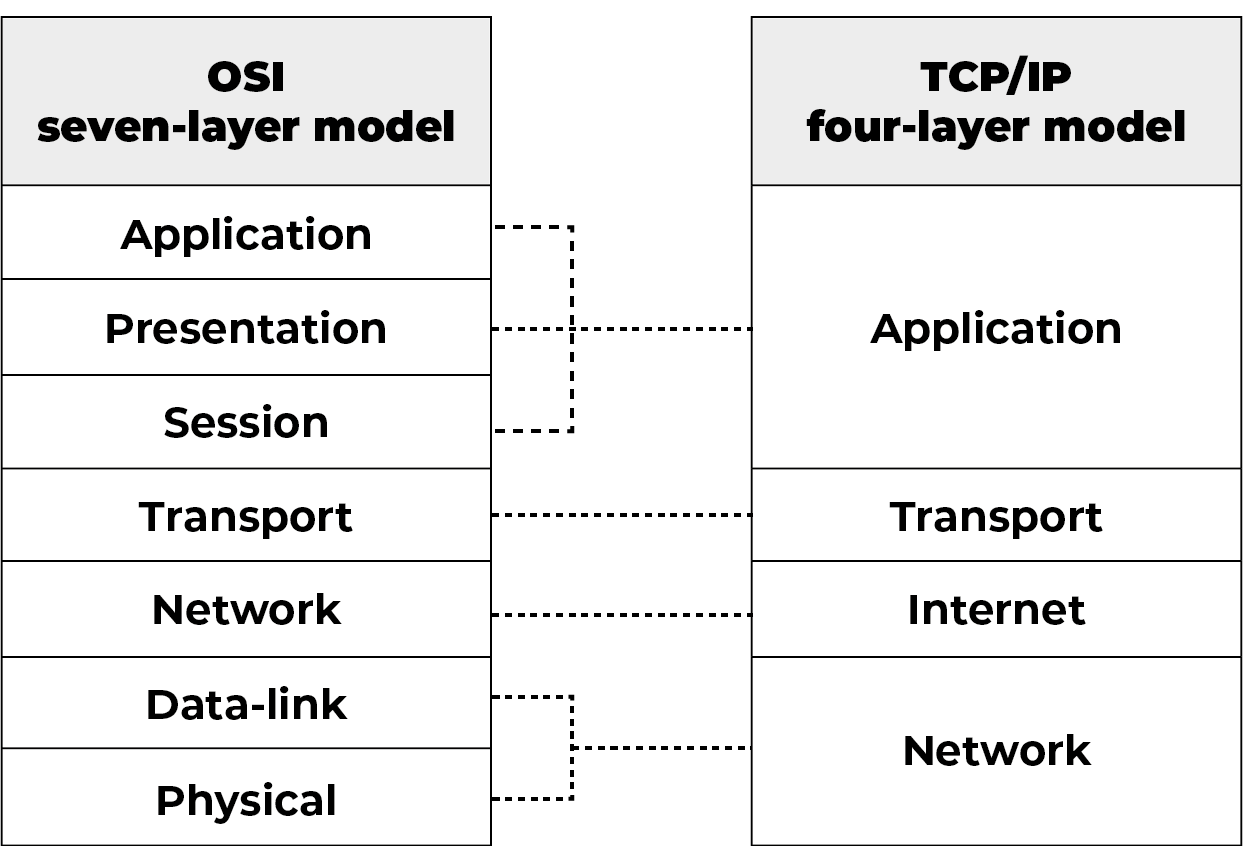
TCP/IP is responsible for full-fledged internet data connectivity and transmitting the data end to end by providing other functions, including addressing, mapping and acknowledgment. TCP/IP contains four layers, which differ slightly from the OSI model.
The technology is so common that one would rarely use the full name. In other words, in common usage the acronym is now the term itself.
TCP/IP
Nearly all computers today support TCP/IP. TCP/IP is not a single networking protocol – it is a suite of protocols named after the two most important protocols or layers within it – Transmission Control Protocol and Internet Protocol.
As with any form of communication, two things are needed: a message to transmit and the means to reliably transmit the message. The TCP layer handles the message part. The message is broken down into smaller units, called packets, which are then transmitted over the network. The packets are received by the corresponding TCP layer in the receiver and reassembled into the original message.Internet Protocoll
The IP layer is primarily concerned with the transmission portion. This is done by means of a unique IP address assigned to each and every active recipient on the network.
In other words, when a message is sent, it is broken into many packets that must reach their destination. The IP portion of the TCP/IP makes sure they arrive at the correct location by traversing different paths. Each packet is forwarded through all gateway nodes on the network by checking the IP address of the receiver.
The TCP portion first ensures that the connection between sender and receiver is maintained from before the first packet is sent to after the last one is reassembled. The TCP is then responsible for assembling all the packets in the right order, requesting missing packets to be sent back, and then provides a confirmation to the sender that the message was received correctly.
TCP/IP is considered a stateless protocol suite because each client connection is newly made without regard to whether a previous connection had been established.
Common protocols of TCP/IP include the Hyper Text Transfer Protocol(HTTP) and Secure HTTP (HTTPS) to handle communication between a web browser and a web server, and the File Transfer Protocol (FTP) to handle transmission of data between computers.
TCP/IP models are divided in four layers:
- Application Layer: Handles the details of communication at the application level.
- Transport Layer: Establishes and maintains a data connection and exchange between two devices.
- Network Layer: Also known as the internet layer, it handles the movement of packets around the network and across other networks.
- Physical Layer: It handles the physical parts of the communication between hosts within the same network using wireless connections, ethernet cables, and so on. It is also called the data link layer or interface layer.
What is the Full Form of TCP/IP?
The full form of TCP/IP is Transmission Control Protocol/Internet Protocol. TCP/IP is a set of networking protocols that define how computers communicate over a network Protocol. The Internet, which is a global network of networks, relies on TCP/IP to connect computers and devices around the world. Internet Protocol
Brief on Transmission Control Protocol/Internet Protocol
Transmission Control Protocol (TCP) is a transport layer protocol used to ensure the reliable delivery of data packets from one device to another. It does this by establishing a virtual connection between the sender and the receiver, and then dividing the data into small packets that are transmitted over the network. If any of the packets are lost or corrupted during transmission, TCP will automatically retransmit them until they are successfully received by the destination device.
Internet Protocol (IP) is a network layer protocol used to route data packets across a network. It does this by assigning a unique numerical address (called an IP address) to each device on the network. When a device wants to send data to another device, it sends the data in the form of packets to the destination device’s IP address. The IP protocol routes the packets to the correct device, even if the devices are on different networks or in different locations.
Together, TCP and IP form the foundation of modern computer networking and the Internet. They allow devices to communicate with each other and exchange data, regardless of the type of device or the location of the device. Internet Protocol
Who invented Transmission Control Protocol/Internet Protocol
TCP/IP was developed in the 1970s by the U.S. Department of Defense (DoD) as a way to connect different computer networks.
The development of TCP/IP was led by a team of researchers, including Vint Cerf and Robert Kahn. Cerf and Kahn are often referred to as the “fathers of the Internet,” because they played a key role in the development of the Internet as we know it today.
Why was the Transmission Control Protocol/Internet Protocol developed?
TCP/IP was developed in the 1970s by the U.S. Department of Defense (DoD) as a way to connect different computer networks. At the time, there were many different networking protocols in use, but none of them were compatible with each other. This made it difficult for computers on different networks to communicate with each other.
The DoD wanted to create a networking protocol that could be used to connect their various computer networks, including ARPANET, which was a precursor to the Internet. They also wanted a protocol that could withstand a nuclear attack, so they created a protocol that was decentralized and could route around damage.
The TCP/IP protocol was designed to be simple and flexible, so that it could be easily implemented on a wide range of computers and devices. It was also designed to be extensible, so that new features and functions could be added as needed.
TCP/IP was first used to connect computers on the ARPANET in 1983, and it quickly became the dominant networking protocol for the Internet. Today, TCP/IP is used by virtually all computers and devices connected to the Internet, and it is the foundation of modern computer networking.
Objectives of Transmission Control Protocol/Internet Protocol
The main objectives of TCP/IP are to:
- Provide a standard set of rules and protocols for how computers should communicate over a network.
- Allow computers to communicate with each other, regardless of their location or the type of device they are using.
- Ensure the reliable delivery of data packets from one device to another.
- Provide a way to route data packets across a network, even if the network is damaged or disrupted.
- Allow different types of networks to be connected and work together, such as local area networks (LANs), wide area networks (WANs), and the Internet.
- Enable the creation of new applications and services that rely on networking and the exchange of data between devices.
Get the largest list of Opposite Words in English here.
Functions of Transmission Control Protocol/Internet Protocol
The main functions of TCP/IP are:
- Transmission Control Protocol (TCP): TCP is a transport layer protocol that is responsible for establishing a virtual connection between a sender and a receiver, and for ensuring the reliable delivery of data packets from one device to another. It does this by dividing the data into small packets, adding a header to each packet with information about the packet, and transmitting the packets over the network. If any of the packets are lost or corrupted during transmission, TCP will automatically retransmit them until they are successfully received by the destination device.
- Internet Protocol (IP): IP is a network layer protocol that is responsible for routing data packets across a network. It does this by assigning a unique numerical address (called an IP address) to each device on the network. When a device wants to send data to another device, it sends the data in the form of packets to the destination device’s IP address. The IP protocol routes the packets to the correct device, even if the devices are on different networks or in different locations.
- Domain Name System (DNS): DNS is a service that translates human-readable domain names (such as www.example.com) into numerical IP addresses that computers can understand. This allows users to access websites and other online resources using easy-to-remember names, rather than having to remember long strings of numbers.
- Network Address Translation (NAT): NAT is a technique that allows devices on a private network (such as a home network) to access the Internet using a single public IP address. NAT hides the IP addresses of the devices on the private network, allowing them to communicate with the outside world while still protecting their privacy.
Features of Transmission Control Protocol/Internet Protocol
The main features of TCP/IP are:
- Virtual connection: TCP establishes a virtual connection between the sender and the receiver, which allows the devices to communicate with each other and exchange data in a reliable manner.
- Packet-based transmission: TCP divides the data into small packets and adds a header to each packet with information about the packet. These packets are transmitted over the network and reassembled by the receiver.
- Flow control: TCP includes flow control mechanisms to prevent the sender from overwhelming the receiver with too much data.
- Error detection and correction: TCP includes error detection and correction mechanisms to ensure the integrity of the data being transmitted. If any errors are detected, TCP will automatically retransmit the data until it is successfully received by the destination device.
- Congestion control: TCP includes congestion control mechanisms to prevent the network from becoming overloaded with too much data.
- End-to-end communication: TCP provides end-to-end communication between the sender and the receiver, which means that the data is transmitted directly from the sender to the receiver, rather than being passed through intermediaries.
- Interoperability: TCP/IP is a standard protocol that is used by virtually all computers and devices that are connected to a network or the Internet. This makes it easy for different types of devices and systems to communicate with each other and exchange data, regardless of their manufacturer or operating system.
Applications of Transmission Control Protocol/Internet Protocol
TCP/IP is used by a wide range of applications and services, including:
- The World Wide Web: The World Wide Web (WWW) is a vast network of interconnected documents and other resources, accessed via the Internet. It relies on TCP/IP to transmit data between servers and clients (web browsers).
- Email: Email is a popular communication tool that allows users to send and receive messages over the Internet. It relies on TCP/IP to transmit messages between email servers and clients (email programs).
- File Transfer Protocol (FTP): FTP is a protocol used to transfer files over the Internet. It relies on TCP/IP to transmit data between FTP servers and clients (FTP programs).
- Telnet: Telnet is a protocol used to remotely access and control computers over the Internet. It relies on TCP/IP to transmit data between the remote computer and the local computer.
- Remote Desktop Protocol (RDP): RDP is a protocol used to remotely access and control computers over a network. It relies on TCP/IP to transmit data between the remote computer and the local computer.
- Online gaming: Many online games rely on TCP/IP to transmit data between game servers and clients (game programs).
- Voice over IP (VoIP): VoIP is a technology that allows users to make phone calls over the Internet. It relies on TCP/IP to transmit voice data between devices.Protocol
Users of Transmission Control Protocol/Internet Protocol
TCP/IP is used by virtually all computers and devices that are connected to a network or the Internet. This includes:
- Personal computers: TCP/IP is the primary protocol used by personal computers to connect to the Internet and communicate with other computers.
- Servers: Servers, which are powerful computers that provide services to other computers, also use TCP/IP to communicate with clients (other computers that use the services provided by the server).
- Mobile devices: Mobile devices, such as smartphones and tablets, use TCP/IP to connect to the Internet and communicate with other devices.
- Internet of Things (IoT) devices: TCP/IP is also used by a wide range of IoT devices, which are devices that are connected to the Internet and can communicate with other devices. Examples of IoT devices include smart home appliances, smart thermostats, and smart security cameras. Protocol
Benefits of Transmission Control Protocol/Internet Protocol
TCP/IP has many benefits, including:
- Interoperability: TCP/IP is a standard protocol that is used by virtually all computers and devices that are connected to a network or the Internet. This makes it easy for different types of devices and systems to communicate with each other and exchange data, regardless of their manufacturer or operating system.
- Reliability: TCP/IP is designed to ensure the reliable delivery of data packets from one device to another. It does this by establishing a virtual connection between the sender and the receiver, and by retransmitting any packets that are lost or corrupted during transmission.
- Scalability: TCP/IP is a flexible protocol that can be used to connect a small local area network (LAN) or a large global network, such as the Internet. It can also be easily expanded to accommodate new devices and applications as they are added to the network.
- Security: TCP/IP includes built-in security measures, such as encryption and authentication, to protect the privacy and integrity of data transmitted over the network.
- Simplicity: TCP/IP is a simple protocol that is easy to implement and use. It is based on a clear set of rules and standards, which makes it easy for developers to create applications and services that rely on networking and the exchange of data between devices.
Limitations of Transmission Control Protocol/Internet Protocol
While TCP/IP is a powerful and widely-used protocol, it does have some limitations:
- Complexity: TCP/IP is a complex protocol that requires a certain level of technical expertise to implement and use. This can make it difficult for non-technical users to understand and troubleshoot problems that may arise.
- Overhead: TCP/IP adds a significant amount of overhead to the data that is transmitted over a network. This overhead includes headers and other control information that is added to the data packets. While this overhead is necessary for the proper functioning of the protocol, it does add to the amount of data that needs to be transmitted, which can impact the overall performance of the network.
- Limited support for real-time applications: TCP/IP is not well-suited for real-time applications that require low latency, such as online gaming or voice over IP (VoIP) calls. This is because TCP/IP is designed to ensure the reliable delivery of data packets, rather than minimizing latency.
- Security vulnerabilities: While TCP/IP includes built-in security measures, it is still vulnerable to security threats, such as hacking and cyber attacks. Network administrators must be vigilant in securing their networks and protecting against these threats. Internet Protocol
Disclaimer ||
The Information provided on this website article does not constitute investment advice,financial advice,trading advice,or any other sort of advice and you should not treat any of the website’s content as such.
Always do your own research! DYOR NFA
Coin Data Cap does not recommend that any cryptocurrency should be bought, sold or held by you, Do Conduct your own due diligence and consult your financial adviser before making any investment decisions!